
Audio By Carbonatix
Background
For the past two weeks, I have followed some media stories concerning the linking of multiple phone numbers to national identity cards in Ghana (also known as the Ghana Card).
The concerns are that unscrupulous persons are able to clandestinely link their SIM card, also known as a subscriber identity module, which is a smart card that stores identification information that pinpoints a smartphone to a specific mobile network to the Ghana Card of unsuspecting members of the public. This essentially creates concerns around identity theft and related identity-base risk when these phone numbers are engaged in any sort of malpractice and crime.
The risk outcome of the linking SIM-to-Ghanacard process can be traced to data integrity, data integrity is an integral component of the Data Protection Act of Ghana under the principles that cover data quality and data security, and it is further an obligation on data controllers to ensure that data quality principles are applied.
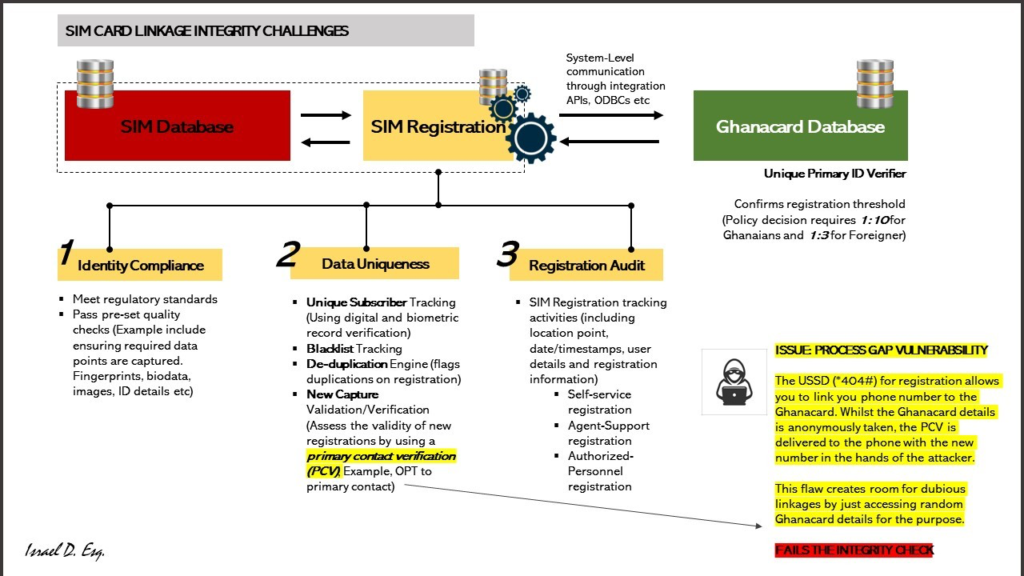
As a matter of fact, from 1st October 2021 when the SIM re-registration exercise commenced in Ghana until after its extension sometime on 31st July 2022 and the subsequent new deadline on 30th September 2023, the Minister in charge made it emphatically clear that the exercise was meant to achieve integrity of the SIM Database for the service providers by using the national identity database to ensure unique SIM subscribers.
Therefore in the process, citizens are required to validate and verify their SIM cards against the national identity database through their various telecom service providers. The exercise received legislative backing through substantive national identity laws and sub-legislations covering the SIM re-registration.
The Logic Flaw Issue
The policy position of the registration and verification process was that Subscribers who are Ghanaians would be able to register ten SIM cards to one Ghanacard (e.i. 1:10 SIM to Ghanacard link ratio), the process also made provision for three SIM cards to one Ghanacard for foreigners (e.i. 1:3 SIM to Ghanacard link ratio). In summary, one can have ten SIM cards registered to their Ghanacard number.
With the benefit of hindsight and repeating the process of registration via a *404# USSD services, the clandestine multiple linkages are leveraging on what I will term a process gap vulnerability (PGV), which can be categorized as a logic flaw in the process design. The PGV as earlier stated, does exist in the USSD registration, it has not been determined at the writing of the article if this is repeatable in the web/mobile application too.
The vulnerability manifests because when a user attempts to register (or link) a SIM to a Ghanacard; the system allows entry of the Ghanacard details intended to be linked with the SIM, and in the process, a one-time password (OTP) is sent for verification, now instead of using a primary contact verification (PCV), which normally should be the first ever SIM registered to the Ghanacard in question, the system by design delivers the verification to the new number attempting the linkage, the OTP is then potentially delivered to the attacker or the unscrupulous person doing the clandestine SIM-linkage. Indeed, needless to say, the Ghana Card details are taken by the system based on a user-trust-process rather than a system-independent validation of the source, I hazard a guess that this was for operational efficacy and, therefore, it would have been essential to resolve the PGV flaw by allowing the OTP to delivered to the PCV, and therefore give the original Ghanacard holder the verification leverage, and in the absence of that opening up for the ongoing clandestine registration.
Best Practice
Let me attempt to pass on an opinion on best practices. The ideal situation is that such a system should have three levels of data integrity check both at the process and data storage. Without being unnecessarily verbose, we can start firstly with “identity compliance”, this level is designed to meet regulatory standards and pass pre-set quality (Examples include ensuring required data points are captured. Fingerprints, biodata, images, ID details, etc)
The second level proposed is “data uniqueness”, at this level of integrity check, the system has to focus on the uniqueness of subscribers using digital and biometric record verification processes (it was indicated that this process is currently infused in the current system), still on this level the system should also be able to check for blacklisted subscribers for the purposes of crime, national security or reported malfeasance based on service level agreement violations. Still, under the data uniqueness level, it is expected that the de-duplication engine should be implemented to flag duplicated registration where necessary and also the new capture feature validation which assesses the validity of new registrations by using a PCV; for example, delivery of the OTP to PCV.
The third and final best practice for data integrity is proposed as “registration audit” (normally found with platforms like the one under discussion), SIM Registration tracking activities (including location point, date/timestamps, user details, and registration information); this process must cover self-service registration, agent-support registration, and authorized-personnel registration to ensure that the entire supply chain in the process of registration can be tracked even in the event of clandestine SIM registrations.
Conclusion
The writer notes that there are different components of the registration systems, which may have independent functions and access-level requirements may vary depending on internal policies, business needs, and statutory obligations among others. It will be ideal for the national identity database to have some level of “true” integration with the SIM registration database; it may vary from real-time, delayed, or on-demand integrations to ensure that the national identity database at all material times necessary will have a recent version of the SIM registration records to ensure the ongoing data integrity touted as the crux of the SIM re-registration exercise a consistent reality.
In a nutshell, the SIM re-registration is an exercise worth the country's investment and efforts, it is important to pay attention to the data integrity issues which undoubtedly even if we are pretentious about its existence may cause the true value of this investment.
*****
Desmond Israel (GW Law Merit Scholar | Lawyer & Data Privacy/Information Security Practitioner | Founder, Information Security Architects Ltd | Research Lead, Child Safety Framework for the Metaverse, XRSI -California | Affiliate, Child Online Africa)
Latest Stories
-
Joy FM’s iconic 90’s Jam returns tonight: Bigger, better, and packed with nostalgia
34 minutes -
Uproar as UG fees skyrocket by over 25% for 2025/2026 academic year
2 hours -
Japan PM joins fight for more female toilets in parliament
3 hours -
Ga Mantse declares war on fishing industry child labour
3 hours -
Adom FM’s ‘Strictly Highlife’ lights up La Palm with rhythm and nostalgia in unforgettable experience
4 hours -
OMCs slash fuel prices as cedi gains
5 hours -
Around 40 dead in Swiss ski resort bar fire, police say
6 hours -
AFCON 2025: Aubameyang and Nsue make history among oldest goalscorers
7 hours -
AFCON 2025: How Kwesi Appiah’s Sudan qualified for round of 16 without scoring any goal
8 hours -
Ghana is rising again – Mahama declares
8 hours -
Firefighters subdue blaze at Accra’s Tudu, officials warn of busy fire season ahead
9 hours -
Luv FM’s Family Party In The Park ends in grand style at Rattray park
9 hours -
Mahama targets digital schools, universal healthcare, and food self-sufficiency in 2026
9 hours -
Ghana’s global image boosted by our world-acclaimed reset agenda – Mahama
9 hours -
Full text: Mahama’s New Year message to the nation
9 hours

