How did we get here? Suddenly the world as we knew it came to a grinding halt and tottered on the brink of despair. In a swift moment, our sanity became questioned, our livelihoods and freedom of movement threatened by an invisible enemy called Corona that spread fear and panic worldwide.
Now it has become clear that this is more than just a public health emergency because it also poses a significant threat to our economic and national security interests. As we are trying to grapple with the drastic changes in these insipid times, cybercriminals are also quickly taking advantage of the global panic caused by the coronavirus pandemic.
Last week the U.S. Federal Trade Commission reported that approximately $12 million was lost to coronavirus-related scams according to consumer reports reviewed this year. Cybercriminals are obviously taking advantage of the pandemic to lure consumers using various attack vectors including social media, phone calls, text messages and phishing emails.
Security telemetry data obtained depicts that since March there had been a surge in the number of coronavirus outbreak related phishing emails and at the beginning of February 2020, a sudden spike recorded in the registration of domains associated with fraudulent COVID-19 themed extortions and financial scams surrounding the purchase of medical supplies including face masks and PPEs as an example.
Curated threat research here in this article provides a brief on COVID-19 threat intelligence taxonomy which I hope will make the reader more aware of securing his/her business and personal interactions in the digital world. In this article I will provide you with some insights into how cyber threat actors have been shifting their tactics during the coronavirus pandemic.
Malware in WHO scam email attachment
During the pandemic, cybercriminals have taken advantage of the situation and are preying on the fear and doubts of individuals by impersonating communications from reputable organizations such as the World Health Organization, the Center for Disease Control and Prevention and John Hopkins University. Right here at home we should naturally be on the lookout for phishing emails and rogue communications impersonating local Ghanaian government ministry, department and agency websites, NGOs, universities and businesses in the healthcare supply chain.
Here is an example of a malicious spam email which mentions that new research on COVID-19 has proven to be effective and the WHO has therefore decided to share a PDF file containing information on safety measures and preventive vaccination. A malware laden PDF attachment was sent in this email purported to be communications from the WHO.

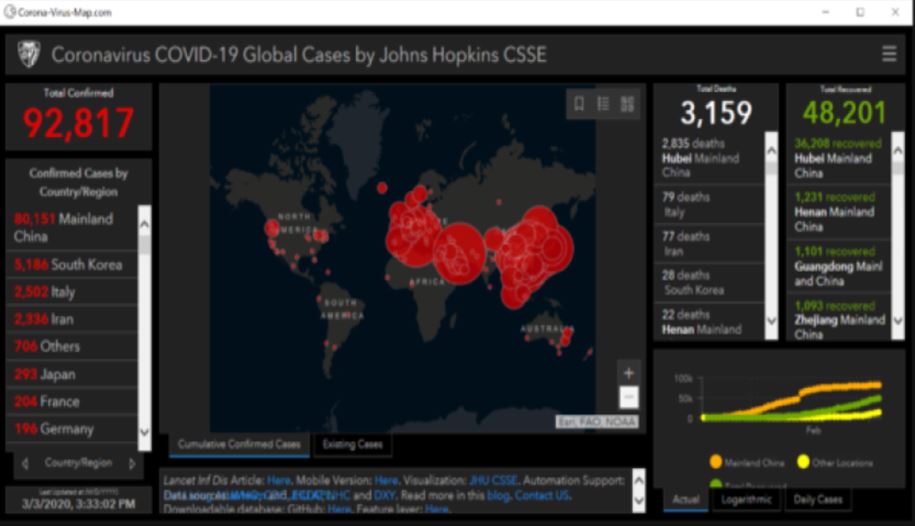
Security researchers recently discovered a malicious software application that claimed to provide an up-to-date coronavirus heat map just like the one on the John Hopkins University website which is a popular COVID-19 dashboard for people who want to stay abreast on the virus outbreak.
The malicious software was found to contain a type of spyware that steals usernames, passwords, credit card numbers and browser cookies. According to threat analysis, the malicious coronavirus map is delivered through malicious online ads, social pretexting, malicious email attachments and software vulnerabilities on user endpoint and mobile devices.
Attacks against the remote workforce
An interesting phenomenon we are seeing today in the formal services sector has been the dramatic shift from the traditional ways of working especially within the corporate and technology driven business workforce to a remote teleworking model.
Figures released by VPN provider NordVPN revealed that global use of its virtual private network technology had increased by 165% since 11th March. A business VPN allows users to securely connect to corporate networks to access data and applications from anywhere. Cybercriminals have already started taking advantage of this massive shift to remote working by exploiting vulnerabilities in VPNs and other remote networking tools in order to launch attacks against remote workers.
Today many organizations are leveraging videoconferencing technology such as Zoom and WebEx to have daily work meetings. Security researchers found out earlier this month that attackers were able to eavesdrop in your private Zoom meetings that were not protected by a password.
Cyber threat actors have been able to modify existing or created new tools that scan for upcoming scheduled Zoom meetings, revealing information about the meeting link, meeting dates and times, the name of the meeting organizer and any other information provided surrounded the meeting topic.
Cybercriminals have also very recently started selling Zoom account credentials on the Internet. These stolen credentials could be used to impersonate your identity and organize meetings with your business partners and clients to perform other sophisticated attacks or gain unauthorized access to corporate data. It has become quite clear that threat actors are shifting their focus to attack employee home networks and personal emails to gain unauthorized access to corporate VPN credentials.
Reported cyber attacks during the pandemic
Italy’s social security website was recently hit by cyber attackers in a denial of service attack causing it to shut down just as Italian citizens began filing their applications for coronavirus benefits. The INPS notified the appropriate authorities of a data breach at the beginning of this month with possible violations of users private and personal information. As part of the Italian government’s initial response to the lockdown and the economic crisis, all self-employed workers were given a 600 euros payout, however most users were unable to access the website to complete their application requests.
The German government potentially lost tens of millions of Euros in COVID-19 phishing attacks as cybercriminals cloned an official government website that was setup to distribute financial aid. The threat actors lured unsuspecting users to their fake websites by distributing links via phishing emails in a campaign that spanned from the middle of March to the first week in April before being detected. What the attackers did was file for government financial aid on behalf of legitimate users and changed the bank account details where the funds were to be disbursed.
A University Hospital in the Czech Republic, in the city of Brno was hit by a cyber-attack which was severe enough to disrupt urgent surgical procedures resulting in the need to refer new acute cases to another University Hospital located close by. The Brno University Hospital was also being used as the biggest COVID-19 testing center and laboratory in the country.
These are very insidious attacks that prey on the current distractions and anxiety of remote staff who are also overwhelmed by the growing deluge of misinformation being spread. Please stay vigilant to protect yourselves from any coronavirus scams and phishing attacks.
In the news, it has been alleged that hackers have successfully hacked the accounts of the Bill Gates Foundation, the CDC, World Bank, National Institute of Health, WHO and the biolab in Wuhan where the coronavirus had initially undergone laboratory research and also reported to be ground zero for the contagion. It seems likely that based on the conspiracy theories surrounding the virus outbreak, these hackers went on a hacking spree on the quest to find out the truth behind the pandemic. It has been reported that thousands of emails, documents usernames and passwords have been leaked online.
Securing your remote workforce
Let us also be mindful of the fact that employees working from home are facing immense stress, anxiety and distractions and are more vulnerable now more than ever to phishing attacks. Coronavirus has come to disrupt the global business supply chain and will encourage IT business leaders to think more seriously on the automation of some key IT processes. Even after the pandemic, management of organizations will likely carefully rethink their investment strategies especially when it comes to spend on things such as sponsorship of public conferences and other notable corporate social networking events.
The government of Ghana has done a fantastic job at containing the crisis however in the foreseeable future it should demand a new kind of pandemic counter-intelligence strategy to ensure they have the right systems and structures in place to withstand the effects of and respond in time to another global pandemic. We urge that you stay vigilant to protect yourselves from any attacks. In the meantime, here are a few things you can do to address the growing security and privacy concerns of your remote workforce during this pandemic season.
Phishing emails and scam protection
- Urge employees to visit only trusted sources of information for critical updates
- Sensitize employees to spot phishing emails via regular security awareness training campaigns
- Keep software and security patches up to date on employee mobile devices and endpoint systems
- Employ the use of AV, email gateway spam filtering technology and two-factor authentication
Remote infrastructure management
- Establish policies and procedures that enable employees to work securely from home
- Use a VPN solution to access corporate data and systems and ensure they are fully patched
- Ensure VPNs can handle the load of all your employees accessing corporate data and services at once
- Enable multifactor authentication to protect VPN credentials from unauthorized account takeovers
- Identify which systems cannot be accessed or administered remotely and come up with policies and workarounds to ensure continuity of critical IT operations
- Where possible enable cloud agents to keep home devices up to date with critical security and other 3rd party software updates
- Use mobile device management (MDM) tools to set up devices with a standard configuration, and also to remotely lock devices, erase data or retrieve backup in the event that is needed
Protecting employee home networks
- Where possible separate employee devices for work and private or personal use
- Consider using secure wireless connections (e.g. WPA2) and stronger Wi-Fi passwords at home
- Ensure that your employees download Android mobile applications only from the Google Play store.
- Use stronger credentials to protect your mobile devices to secure both company and personal data
- Guide employees to upgrade home Internet router firmware and change default router settings
Videoconferencing security
- Ensure passwords for Zoom meetings and other videoconferencing platforms are enabled by default
- Disable the ‘allow participants to join the meeting before the host arrives’ option in Zoom
- Change your Zoom account passwords if you think your account may have been compromised
- Update all videoconferencing software especially Zoom to the latest software security version
Edem Glymin is the lead security and risk consultant for Global Secure Solutions Ghana Limited.
Latest Stories
-
NDC accuses trial judge of bias over order to re-collate outstanding parliamentary results
29 minutes -
WAEC receives additional fund of GH¢35m, urges release of outstanding funds
30 minutes -
Illegal Mining at Songor Lagoon thwarted by Electrochem Ghana Limited Security
51 minutes -
Retain current Majority leadership – NPP Parliamentary Committees to party council
55 minutes -
GIPS applauds Kwesi Acquah on new role as an Associate Professor of Procurement at UCC School of Business
1 hour -
From grass to Gruyère: Unveiling the secrets of Swiss Dairy Excellence
2 hours -
Christmas in Takoradi: Masqueraders takeover principal streets in style
2 hours -
Merdarlock feeds thousands on the street, donates cash gifts to families
2 hours -
NDP’s Christabel Adomako wishes Mahama and Ghanaians a merry christmas
2 hours -
GPL: Christopher Ennin replaces Nurudeen Amadu as Samartex head coach
3 hours -
Fire razes Trinity TV station and church at Krofoum
3 hours -
2024/25 GPL: Asante Kotoko aim for third straight win in clash with Gold Stars
3 hours -
CHAN 2024Q: Black Galaxies leave for Uyo ahead of decider against Nigeria
3 hours -
Livestream of proceedings as NDC challenges High Court’s order for election re-collation
4 hours -
UPSA postpones Vice-Chancellor’s investiture amid alleged legal challenges
5 hours

